Firemon
Who is Firemon?
FireMon is the #1 security automation solution for hybrid cloud enterprises. FireMon delivers persistent network security for multi-cloud environments through a powerful fusion of real-time asset visibility, compliance and automation. Since creating the first-ever network security policy management solution, FireMon has delivered command and control over complex network security infrastructures for more than 1,700 customers located in nearly 70 countries around the world.
Customer Challanges
Network Security Automation
The path to digital transformation is paved with a sophisticated threat landscape, a security staffing shortage, emerging technologies, and the inability to keep up with business demands. See how automation can streamline your security workflows and boost your operational efficiency to drive innovation at the speed of business without sacrificing security.
FireMon Automation delivers a comprehensive blueprint for security process automation that accelerates and streamlines policy management through trusted accuracy, gold standards, and proactive continuous compliance.
Cloud Migration: Field-Tested, Cloud-Secured
- Gain Centralized, Real-Time Visibility
- Embrace Your Hybrid Cloud
- Eliminate Misconfigurations
- Assess Risk in Real-Time
- Achieve Continuous Compliance
Firewall Optimization & Security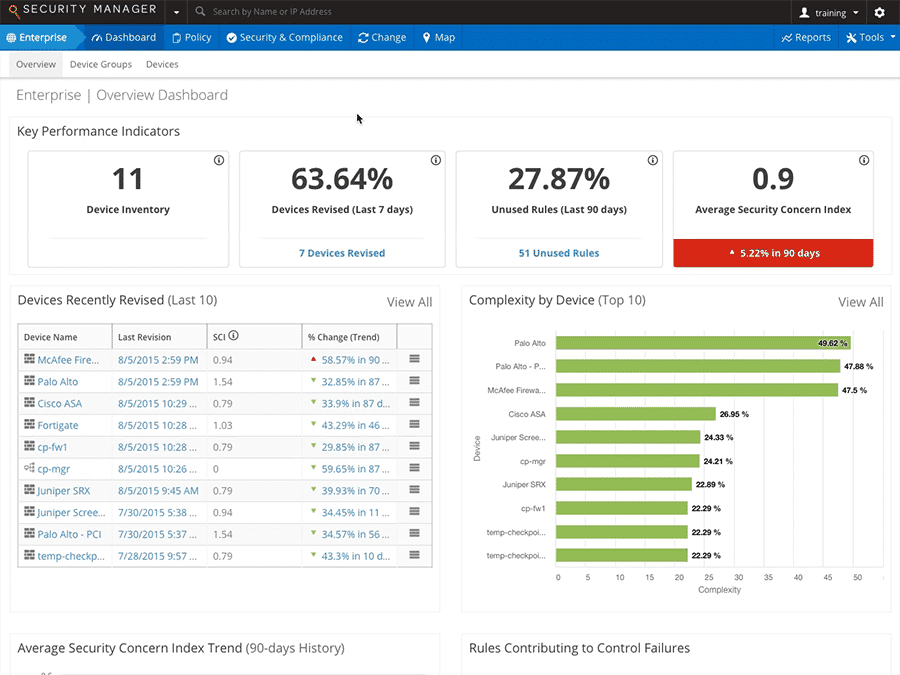
- Eliminate Redundant Rules
- Remove Unused Rules and Objects
- Minimize Excessive Access
- Automate Rule Recertification
- Optimize Security Policies
Security Policy Change Management
- Automate Ticket Tracking
- Automate At Your Pace and Confidence Level
- Analyze Redundant Rules
- Assess Potential Change Impacts
- Automate Rule Review and Implementation
- Automate Rule Removal
Microsegmentation for Zero Trust Networks
Continuous Compliance
Firewall Cleanup
- Eliminate Redundant Rules
- Remove Unused Rules and Objects
- Minimize Excessive Access
- Automate Rule Recertification
- Optimize Security Policies
Network Compliance Reporting & Audit: A Life Hack for Audits
Tough as it may be, compliance is necessary to protect data and applications and to keep services running. The process of preparing for audits, however, can be a grind, time-intensive and painful to pull it all together. It usually takes weeks (or months), which means by the time you’re ready, everything has changed. The digital ink is barely dry before the details become obsolete.
Risk Mitigation
Attack Surface Reduction
The attack surface is the total space for exploit within the infrastructure. Enterprise infrastructures have a habit of moving and changing with little notice or control, making it nearly impossible to see what’s what. You can’t defend what you can’t see.
Those looking to snatch and grab your data hunt for your weaknesses. The only way to get ahead of a cybercriminal is to reduce the battlefield – the attack surface – vulnerable to exploit.
- How does that happen?
- The FireMon Solution
- Vulnerability Management
- Continuous Compliance
- Orchestration
- The FireMon Difference
Risk Modelling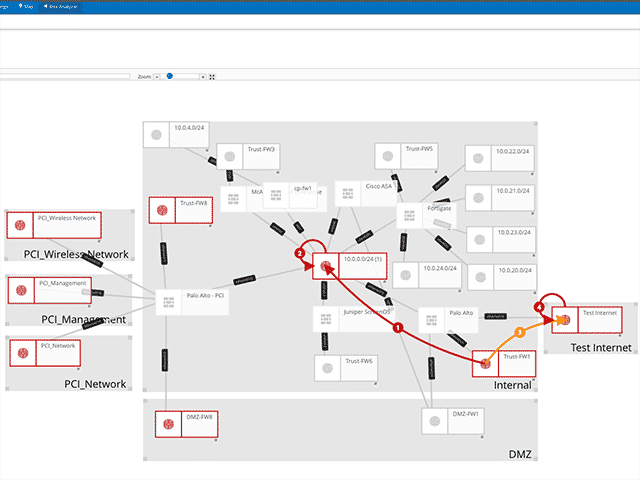
- Calculate Network Reachability
- Simulate Potential Attacks
- Score Attack Simulations
- Analyze “What If” Scenarios
- Remediate Exposures
Network Visibility Monitoring
Lumeta is a real-time visibility, vulnerability, and risk management solution that enables cloud, network, and security teams to find and secure unknown, rogue and shadow clouds, network infrastructure, and endpoints.
Real-Time Situational Awareness
Gain real-time visibility into your dynamic infrastructure including cloud, virtual, physical, software-defined network infrastructure, endpoints, and operational technology (OT)/Internet of Things (IoT). With Lumeta, you can eliminate 100% of your blind spots and monitor changes or unusual behaviors to eliminate any gaps in coverage that may leave you exposed.
100% Hybrid Cloud Visibility
Lumeta discovers, maps and alerts on topology changes across the entire hybrid enterprise, including multi-cloud environments. Delivering a holistic view across all of your physical and virtual/cloud infrastructures, Lumeta CloudVisibility provides an authoritative perspective for your enterprise security operations center (SOC) to prioritize issues for remediation and ensure network protection.
Real-Time Breach Detection
Lumeta monitors the hybrid infrastructure for telltale signs of nefarious activity and prioritizes findings for investigation and remediation. With Lumeta, your threat intelligence feeds are made actionable to correlate a comprehensive understanding of your enterprise’s active IP address space against known threats as new threat data becomes available, and as new endpoints connect to the network.
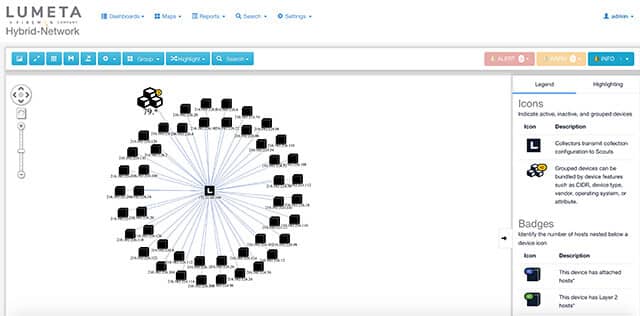 Identify Leak Paths
Identify Leak Paths
Lumeta discovers and monitors every cloud account, network, path and endpoint for changes in real-time to identify new leak paths that are often due to misconfigurations or malicious activity. Lumeta finds inbound and outbound leak paths to the Internet, virtual private cloud, in between network-segmented, firewalled enclaves, or across IoT/OT environments.
Recursive Network Indexing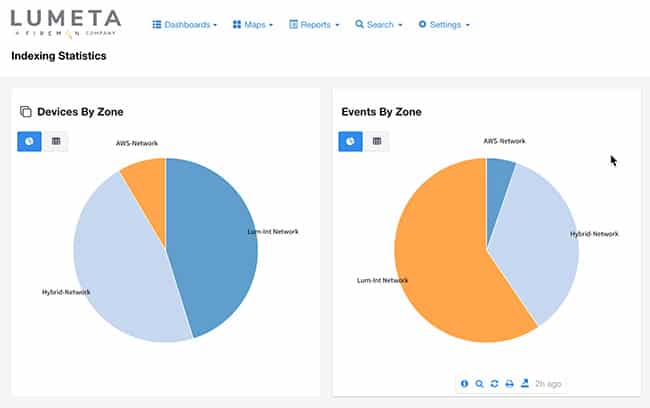
Lumeta uses a unique patent-pending technology to produce a comprehensive network summary that includes a recursively crawling cycle of targeting, indexing, tracing, monitoring, profiling, and displaying a network’s state. Through passive and active methods, you get a view of your entire infrastructure, including cloud instances and assets, as well as all IPv4/IPv6 connections and devices.
Threat & Vulnerability Management
Risk Vulnerability Management
Outside threats have the potential to scale the wall through any access point on the network. However, not all threats are created equal. If the asset is of high value, customer credit card info for example, its compromise would have a bigger impact than that of a lesser-value asset.
FireMon allows network and security teams to map the potential paths an attacker could take based on real-time configuration data and vulnerability scanner feeds. Then it helps prioritize the gaps for remediation, so the most impactful get taken care of first.
How It Is Done

- Reachability analysis calculates how easy it would be for an attacker to reach assets through and assess the potential damage
- Graphical attack paths trace the possible path an attacker might use and identifies where an attack can be stopped with the least amount of time and effort
- Risk scoring measures attack simulations for risk and impact. Re-score once you make improvements to determine the impact of the change.
- Patch simulation patches systems virtually so you can compare various patch scenarios to prioritize efforts to those with the biggest impact
- Access path analysis traces all potential traffic paths, identifies problematic routes and then recommends adjustments to redirect access




















